2025-09-14 21:52:36 +00:00
|
|
|
|
# 特定http网址被chrome浏览器重传时无法成功deny
|
|
|
|
|
|
|
|
|
|
|
|
| ID | Creation Date | Assignee | Status |
|
|
|
|
|
|
|----|----------------|----------|--------|
|
|
|
|
|
|
| OMPUB-902 | 2023-04-17T10:48:48.000+0800 | 杨威 | 已关闭 |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
---
|
|
|
|
|
|
|
|
|
|
|
|
测试环境:信息港LTS环境
|
|
|
|
|
|
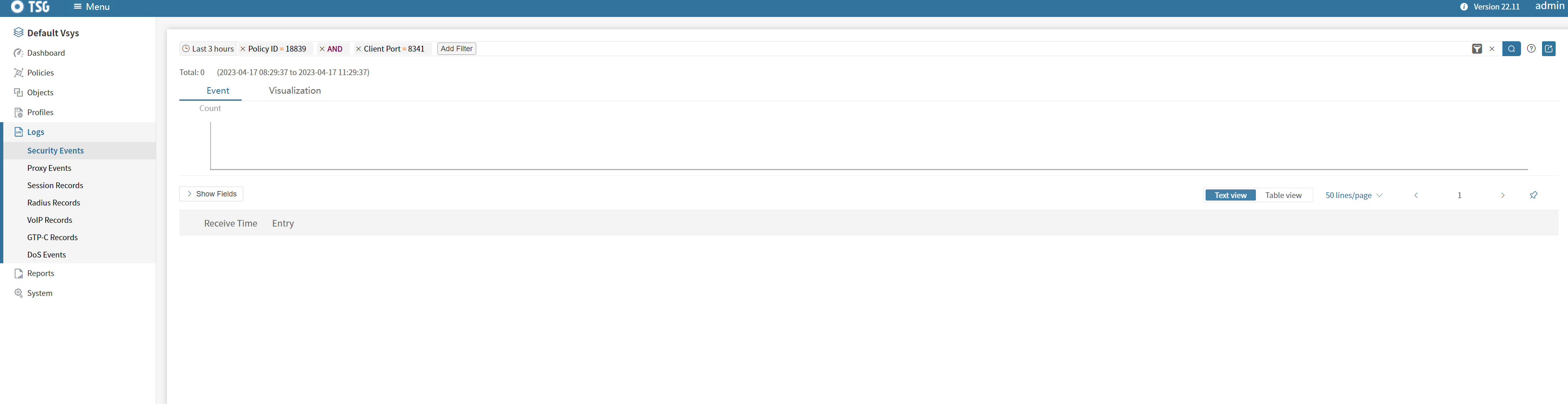
策略ID:18839
|
|
|
|
|
|
策略-URL对象:*hypertext/WWW/
|
|
|
|
|
|
测试网址:http://info.cern.ch/hypertext/WWW/
|
|
|
|
|
|
服务端IP:188.184.21.108
|
|
|
|
|
|
|
|
|
|
|
|
穿透现象:
|
|
|
|
|
|
使用chrome浏览器访问测试网址,可以正常deny,此时不做任何操作,等待浏览器重传,一段时间后穿透。{color:red}查看安全策略日志,发现穿透的那次没有对应日志。查看tcpdump_mesa抓到的包,可以看到对应端口的报文{color}
|
|
|
|
|
|
|
|
|
|
|
|
数据包分析:
|
|
|
|
|
|
clien_188.184.21.108.pcap中的数据为过滤后的,只有客户端访问188.184.21.108的数据包。在客户端8340端口之前(含)的访问都是能够正常阻断的,客户端可以看到rst包。在8341端口时出现穿透,客户端未收到rst,同时查看tcpdump_mesa_188.184.21.108.pcap发现8341端口相关的流量是正常经过了sapp的
|
|
|
|
|
|
|
|
|
|
|
|
!image-2023-04-17-11-26-01-759.png|thumbnail!
|
|
|
|
|
|
!image-2023-04-17-11-26-08-896.png|thumbnail!
|
|
|
|
|
|
!image-2023-04-17-11-30-56-481.png|thumbnail!
|
|
|
|
|
|
**zhangzhihan** commented on *2023-04-19T11:02:18.457+0800*:
|
|
|
|
|
|
|
|
|
|
|
|
在福建也发现了同样的问题,测试网址 https://p.xxt011.com/,访问一开始正常阻断,静置一段时间(大概一小时?)过后自动穿了
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
---
|
|
|
|
|
|
|
|
|
|
|
|
**yangwei** commented on *2023-04-25T08:55:05.398+0800*:
|
|
|
|
|
|
|
|
|
|
|
|
在京版五楼测试环境发现,使用chrome访问被deny网站时,浏览器重试的连接,三次握手成功后,等待超过30秒(平台设置的默认TCP流超时是30秒)才发起HTTP Get请求,触发sapp的超时淘汰,导致穿透。
|
|
|
|
|
|
* 可以通过修改etc/sapp.toml->STREAM->stream.tcp-> timeout参数增加TCP超时时间
|
|
|
|
|
|
|
|
|
|
|
|
会话记录日志没有对应四元组的原因为,sapp认为该会话仅传输了3个包和0个字节,默认发送会话记录的条件是“超过3个包{*}且{*}传输的TCP负载长度大于5”,会话没有满足该条件,因此没有对应的记录。
|
|
|
|
|
|
* 可以修改tsgconf/main.conf->TSG_CONN_SKETCH->tcp_min_bytes,降低对发送TCP负载长度的要求,使当前会话被记录
|
|
|
|
|
|
|
|
|
|
|
|
!image-2023-04-25-08-49-04-674.png|width=1531,height=198!
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
---
|
|
|
|
|
|
|
|
|
|
|
|
**zhangzhihan** commented on *2023-04-25T10:16:56.085+0800*:
|
|
|
|
|
|
|
|
|
|
|
|
调整超时时间后,对该网站连续测试10次,均未穿透。
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
---
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
2025-09-14 22:26:17 +00:00
|
|
|
|
# Attachments
|
2025-09-14 21:52:36 +00:00
|
|
|
|
|
2025-09-14 22:26:17 +00:00
|
|
|
|
Attachment: client_188.184.21.108.pcap
|
2025-09-14 22:27:11 +00:00
|
|
|
|
|
2025-09-14 22:26:17 +00:00
|
|
|
|
[client_188.184.21.108.pcap](https://gfwleak.exec.li/admin/geedge-jira/raw/branch/master/attachment/37386/client_188.184.21.108.pcap)
|
2025-09-14 21:52:36 +00:00
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
2025-09-14 22:26:17 +00:00
|
|
|
|
Attachment: image-2023-04-17-11-26-01-759.png
|
2025-09-14 22:27:11 +00:00
|
|
|
|
|
2025-09-14 22:26:17 +00:00
|
|
|
|

|
2025-09-14 21:52:36 +00:00
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
2025-09-14 22:26:17 +00:00
|
|
|
|
Attachment: image-2023-04-17-11-26-08-896.png
|
2025-09-14 22:27:11 +00:00
|
|
|
|
|
2025-09-14 22:26:17 +00:00
|
|
|
|

|
2025-09-14 21:52:36 +00:00
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
2025-09-14 22:26:17 +00:00
|
|
|
|
Attachment: image-2023-04-17-11-30-56-481.png
|
2025-09-14 22:27:11 +00:00
|
|
|
|
|
2025-09-14 22:26:17 +00:00
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
Attachment: image-2023-04-25-08-49-04-674.png
|
2025-09-14 22:27:11 +00:00
|
|
|
|
|
2025-09-14 22:26:17 +00:00
|
|
|
|

|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
Attachment: tcpdump_mesa_188.184.21.108.pcap
|
2025-09-14 22:27:11 +00:00
|
|
|
|
|
2025-09-14 22:26:17 +00:00
|
|
|
|
[tcpdump_mesa_188.184.21.108.pcap](https://gfwleak.exec.li/admin/geedge-jira/raw/branch/master/attachment/37385/tcpdump_mesa_188.184.21.108.pcap)
|
2025-09-14 21:52:36 +00:00
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|